您當(dāng)前位置: 主頁 > 資訊動(dòng)態(tài) > IT知識(shí)庫 >
IT外包桌面解決方案--SQL注入漏洞過程實(shí)例及解決方案
2020-03-30 16:21 作者:艾銻無限 瀏覽量:
與眾不同的服務(wù)是因?yàn)橛行?/strong>

所有艾銻人可能都知道艾銻無限為客戶提供三種與客戶接觸的方式,一種是產(chǎn)品,一種是技術(shù),還有一種是服務(wù),那這三種所謂的方式構(gòu)建起一個(gè)三角形,這種穩(wěn)固的體系,看起來還不錯(cuò),但我們細(xì)細(xì)思考卻發(fā)現(xiàn)很多企業(yè)也都提供這三種方式與客戶建立一個(gè)長(zhǎng)久的關(guān)系。
那艾銻無限到底與這些企業(yè)有什么區(qū)別呢?有什么明顯的區(qū)別,讓客戶和其他人一看這種服務(wù)就明白是艾銻無限的服務(wù),這個(gè)世界上獨(dú)一無二的服務(wù)呢,大家都看過3D電影吧,無論后來的技術(shù)提升或其他人如何模仿,如何超越,大家首先可能想到的3D電影的代表作是《阿凡達(dá)》,是的這就是獨(dú)一無二,那如何讓我們的三種與客戶建立聯(lián)系的方式也能變的立體呢,我們來看怎樣把這三種方式賦予生命,讓他們與眾不同.
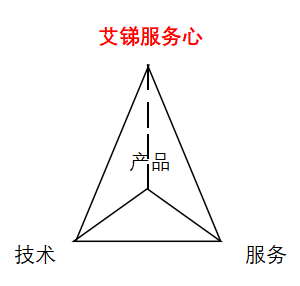
大家可能已發(fā)現(xiàn)原來“艾銻服務(wù)心”讓我們的服務(wù)變的立體,開始有了美感,開始賦予了新的生命,而不是之前人們認(rèn)為的那種“無聊”,沒有生趣的服務(wù),這是一種全新的與客戶建立聯(lián)系的方式,與客戶產(chǎn)生互動(dòng)的方式,這是生命與生命的互動(dòng),這是靈魂與靈魂間的碰撞,就像我們的每一顆蒲公英種子一樣讓每一次與人的接觸都賦予了生命,而不是人與機(jī)器的單調(diào)互動(dòng),更不是那種看起來死氣沉沉的三角形。我們用我們的愛,付出,喜悅轉(zhuǎn)化出我們的誠(chéng)心,細(xì)心,貼心的彼此體驗(yàn),讓更多的三面體不斷去聚合,形成一顆璀璨的鉆石。
SQL注入漏洞過程實(shí)例及解決方案
代碼示例:|
1
2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
public class JDBCDemo3 {public static void demo3_1(){boolean flag=login("aaa' OR ' ","1651561"); //若已知用戶名,用這種方式便可不用知道密碼就可登陸成功if (flag){System.out.println("登陸成功");}else{System.out.println("登陸失敗");}}public static boolean login(String username,String password){Connection conn=null;Statement stat=null;ResultSet rs=null;boolean flag=false;try {conn=JDBCUtils.getConnection();String sql="SELECT * FROM user WHERE username='"+username+"'AND password='"+password+"'"; //此處是SQL注入漏洞的關(guān)鍵,因?yàn)槭亲址钠唇樱瑫?huì)使查詢語句變?yōu)椋篠ELECT * FROM user WHERE username='aaa' OR '' AND password='1651561',此查詢語句是可得到結(jié)果集的,便出現(xiàn)此漏洞stat=conn.createStatement();rs=stat.executeQuery(sql);if(rs.next()){flag=true;}else{flag=false;}} catch (SQLException e) {e.printStackTrace();}return flag;} |
|
1
2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
public static void demo3_1(){boolean flag=login1("aaa' OR ' ","1651561");if (flag){System.out.println("登陸成功");}else{System.out.println("登陸失敗");}}public static boolean login1(String username,String password){Connection conn=null;PreparedStatement pstat=null;ResultSet rs=null;boolean flag=false;try {conn=JDBCUtils.getConnection();String sql="SELECT * FROM user WHERE username=? AND password=?"; //使用?代替參數(shù),預(yù)先設(shè)置好sql格式,就算在輸入sql關(guān)鍵字也不會(huì)被sql識(shí)別pstat=conn.prepareStatement(sql);pstat.setString(1,username); //設(shè)置問號(hào)的值pstat.setString(2,password);rs=pstat.executeQuery();if(rs.next()){flag=true;}else{flag=false;}} catch (SQLException e) {e.printStackTrace();}return flag;}} |
相關(guān)文章
- [網(wǎng)絡(luò)服務(wù)]保護(hù)無線網(wǎng)絡(luò)安全的十大
- [網(wǎng)絡(luò)服務(wù)]無線覆蓋 | 無線天線對(duì)信
- [網(wǎng)絡(luò)服務(wù)]綜合布線 | 綜合布線發(fā)展
- [數(shù)據(jù)恢復(fù)服務(wù)]電腦運(yùn)維技術(shù)文章:win1
- [服務(wù)器服務(wù)]串口服務(wù)器工作模式-服務(wù)
- [服務(wù)器服務(wù)]串口服務(wù)器的作用-服務(wù)維
- [服務(wù)器服務(wù)]moxa串口服務(wù)器通訊設(shè)置參
- [網(wǎng)絡(luò)服務(wù)]網(wǎng)絡(luò)運(yùn)維|如何臨時(shí)關(guān)閉
- [網(wǎng)絡(luò)服務(wù)]網(wǎng)絡(luò)運(yùn)維|如何重置IE瀏覽
- [網(wǎng)絡(luò)服務(wù)]網(wǎng)絡(luò)運(yùn)維|win10系統(tǒng)升級(jí)后
- [辦公設(shè)備服務(wù)]辦公設(shè)備:VPN簡(jiǎn)介
- [辦公設(shè)備服務(wù)]辦公設(shè)備:VPN技術(shù)的要求
 關(guān)閉
關(guān)閉




